** Edit, 9th October — Many EMC products now have patches available **
VNX Series1 VNX Series2 XtremIO VNXe
–Get busy !
On the 24th September, a series of CVE (Common Vulnerabilities & Exposure) incidents were published and have gained significant publicity (and rightly so) due to their potential for catastrophic impact across many product using the BASH shell.
Read all about them here & here
It’s another serious exposure and won’t be long before it’s added to the metasploit libraries for the kiddies.
It’s well documented which commercial products are exploited but what about EMC, VMWare et al ?
The current engineering updates from both companies can be found below and for many products the investigation is continuing;
- VMware assessment of bash Code Injection Vulnerability via Specially Crafted Environment Variables (CVE-2014-6271 CVE-2014-7169, aka “shellshock”)(2090740)
- Bash Code Injection Vulnerability (ShellShock/BashBug) in EMC products. (<– Support Login required)
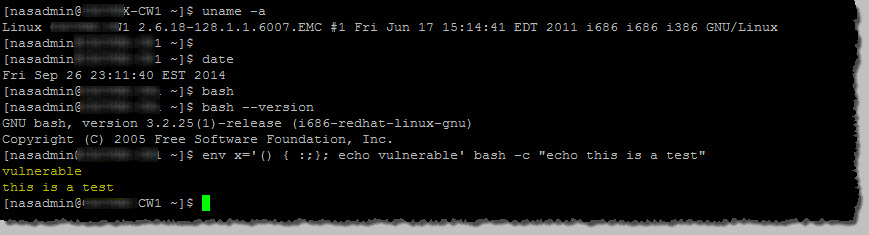
I have tested on a EMC unified VNX system and found it to be vulnerable, as expected per the document above;
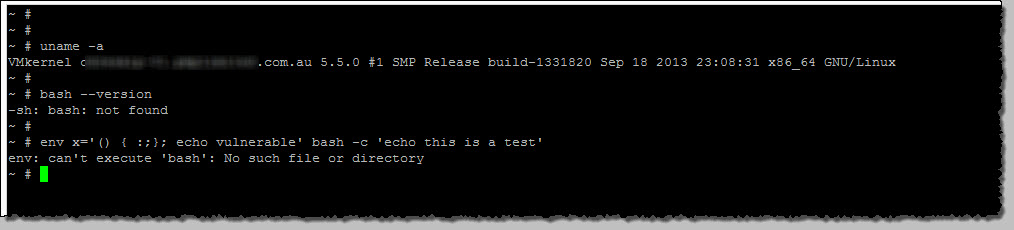
On a (relatively) recent build of ESXi, this won’t be the case. Why ? ESXi uses the busybox platform which does not use BASH, rather ASH.
For S&G’s anyway;
So what’s the message ? As Johnny would say, be Alert but not Alarmed. I don’t see this as a vector that the products in question would be commonly exposed to.
Watch your Vendors notifications pages and patch/mitigate as appropriate.
…….and don’t forget to check if the Internet is on fire